Woke up to a hacked WordPress site? Yeah, been there. It sucks. But listen – you don’t need to freak out or drop cash on expensive security tools just yet.
I’ve cleaned nasty infections off WordPress sites without spending a single dollar. And guess what? You can too.
This isn’t some magic trick. It’s just a brutally effective process that works if you follow it step-by-step. Let’s get into it.
First – Run a Free Scan with Wordfence
Before you start nuking files or panicking, install the free version of Wordfence. It’s in the plugin repo.
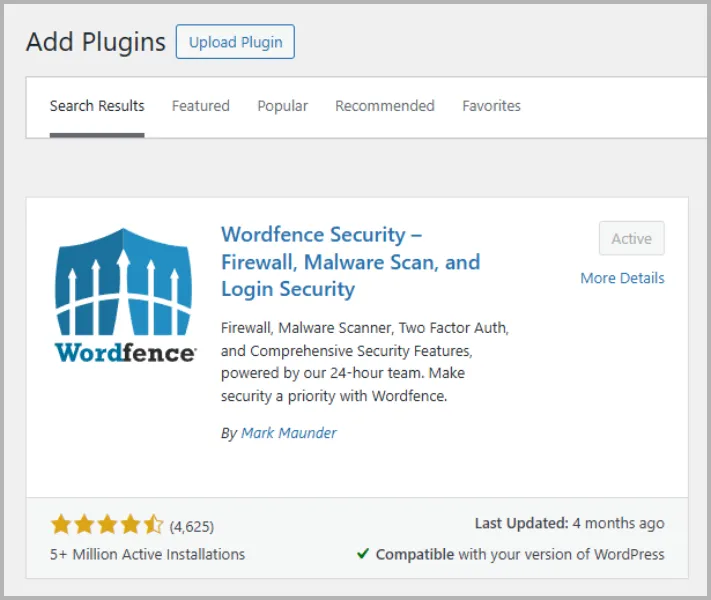
Fire it up, run a full scan, and let it sniff out all the crap – malicious code, shady users, whatever’s hiding under the hood.
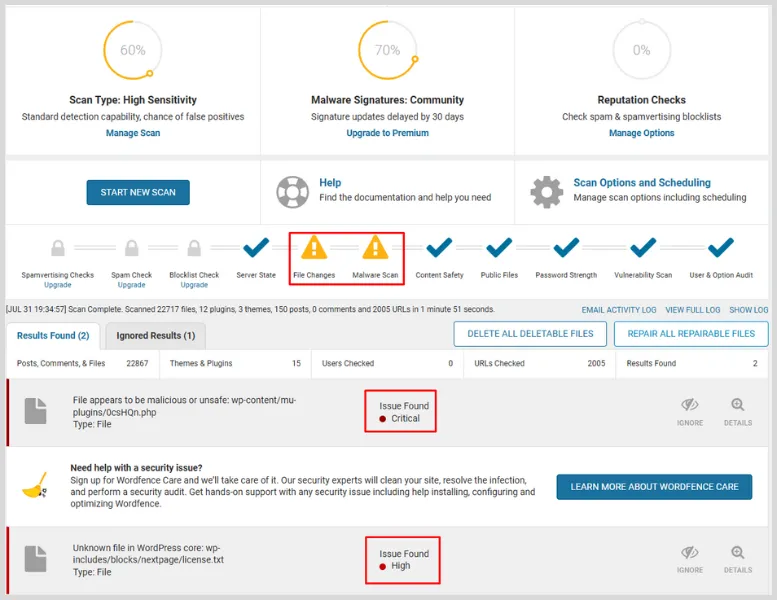
Chances are, the bad stuff is chilling in places like public_html, wp-admin, or wp-includes. But don’t get too hung up on the exact folders – your hosting setup might be different.
For example, if you’re using HestiaCP like I do, the main directory might be something like:
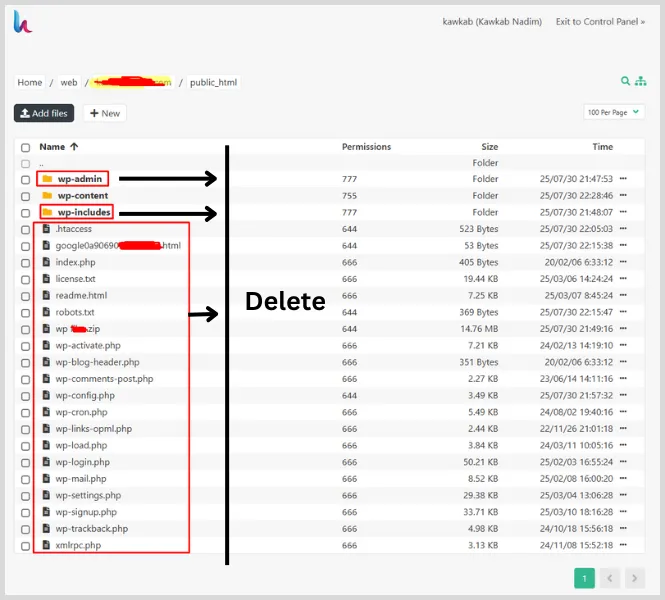
/home/web/yourdomain.com/public_html. Point is — know where your WordPress root lives.
Wipe Out the Core (But Keep wp-content Safe)
Now the fun (read: terrifying) part – deleting stuff. You’re gonna kill off everything except the wp-content folder.
But wait – back up the essentials first:
- wp-config.php
- .htaccess
- robots.txt, ads.txt, and any verification files (Google, Bing, etc.)
Once that’s done, delete:
- wp-admin
- wp-includes
- Everything else in the root (except wp-content and the backup files you just saved)
Yes, I said delete. You’re removing the poisoned flesh to save the patient.
Now, Get Fresh WordPress Files
Head over to wordpress.org, grab the latest version, unzip it, and upload:
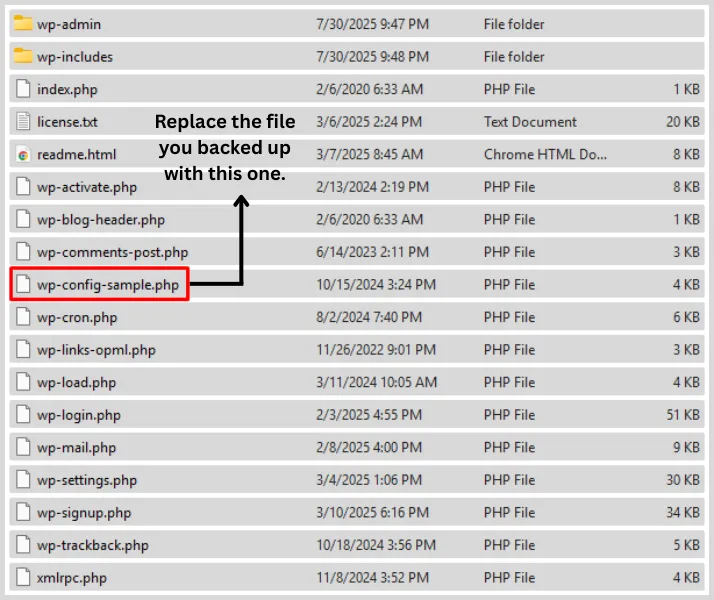
- wp-admin
- wp-includes
- All the core files (leave wp-content alone)
Basically, you’re transplanting a clean heart into your site’s filthy body.
Clean Your Backups Before Putting Them Back
Don’t just upload your backed-up files blindly. That’s how malware comes back like a cockroach. Open those files (wp-config.php, .htaccess, etc.) and look for sketchy code – like eval(), base64_decode(), gzinflate(), or any other junk you don’t recognize.
If you’re not sure what you’re looking at, just copy the code and paste it into ChatGPT. Say something like, “Hey, can you check if this code is malicious?” Let the bot (or your dev friend) help you spot anything shady.
Plugins = Prime Suspects
This is where 90% of malware loves to hide. Go to /wp-content/plugins/, jot down the names of all your plugins, and delete every single one.
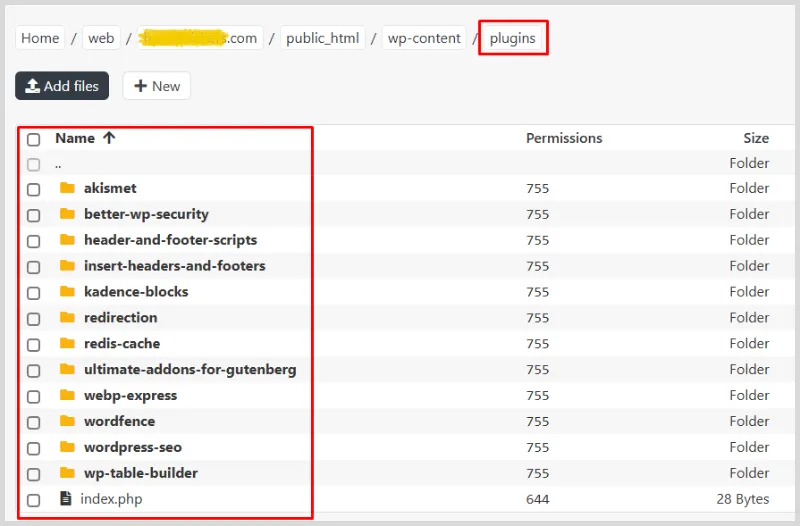
Don’t worry – you’re not losing settings. Most plugin data sits in the database. After you log back into your WordPress dashboard, just reinstall them from the official plugin repo.
Boom. Fresh, clean installs. No malware.
Optional: Deal with Themes and Uploads (If You Must)
Themes usually don’t get hit unless you’ve been using sketchy pirated stuff. If you’re unsure, delete the theme and reinstall a fresh copy from a legit source.
As for the uploads/ folder – leave it unless you spot random .php files hanging out where only images should live. That’s not normal.
Final Cleanup: Lock the Doors
Now that your site isn’t on digital life support anymore, do some housekeeping:
- Kill any suspicious admin users
- Change all passwords (yes, even the strong ones)
- Turn on two-factor authentication
- Re-scan with Wordfence just to be sure
- If Google had flagged your site, go beg Search Console to give you another shot
Bottom Line
You don’t need a security expert or a $99/month firewall to clean your WordPress site. What you do need is a clear plan, a bit of nerve, and a few hours of your time. This method works. It’s not perfect. It’s not pretty. But it gets the job done.
So, yeah – don’t let some punk malware ruin your site. Clean it up, lock it down, and move on with your life.
You got this. For real.
Related Articles about WordPress: